CentOS配置Nginx SSL
在实际应用中,通常是向知名的的CA提交证书申请来申请证书,但某些情况下出于成本的考虑,也可以自己制作证书。这里,我们先创建一个私有的CA根证书,模拟官方的CA,对用户提交的SSL证书进行签名,因此,生成证书的过程分为两部:1)创建CA根证书,2)创建nginx 的SSL证书
关于CA证书(来自百度百科):
CA 也拥有一个证书(内含公钥和私钥)。网上的公众用户通过验证 CA 的签字从而信任 CA ,任何人都可以得到 CA 的证书(含公钥),用以验证它所签发的证书。
如果用户想得到一份属于自己的证书,他应先向 CA 提出申请。在 CA 判明申请者的身份后,便为他分配一个公钥,并且 CA 将该公钥与申请者的身份信息绑在一起,并为之签字后,便形成证书发给申请者。
如果一个用户想鉴别另一个证书的真伪,他就用 CA 的公钥对那个证书上的签字进行验证,一旦验证通过,该证书就被认为是有效的。证书实际是由证书签证机关(CA)签发的对用户的公钥的认证。
证书的内容包括:电子签证机关的信息、公钥用户信息、公钥、权威机构的签字和有效期等等。目前,证书的格式和验证方法普遍遵循X.509 国际标准。
利用OpenSSL生成证书
默认情况下,在CentOS6.5上,OpenSLL是已经安装好的
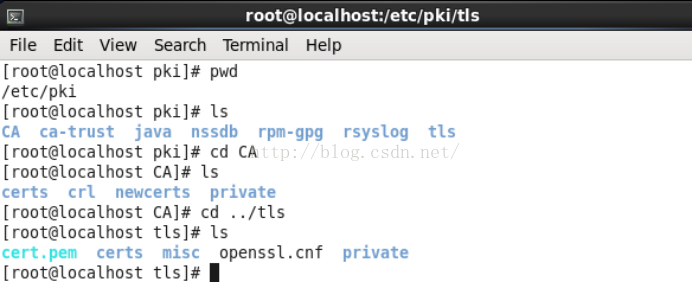
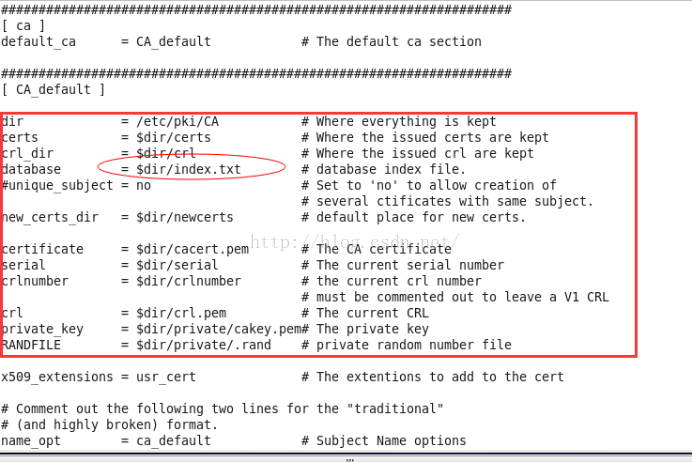
1. 根据/etc/pki/tls/openssl.cnf配置信息,在/etc/pki/目录下创建index.txt文件
生成CA证书
2. 生成rsa根密钥对
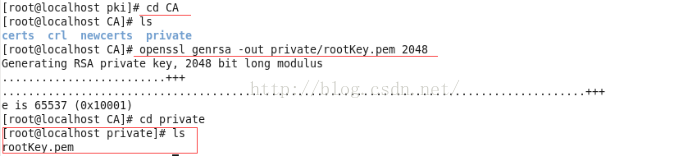
查看一下文件内容
[root@localhost private]# cat rootKey.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAxl7AZiR6n1HW90vkKOmghhRpShiH+Cqtd8MkOa0b6h8er5zN
0pAXqO6rUGYVYjISEZb7yIna5ecG0rlmZMxNwOWPJiV3q4a28CFkXpvCIRRvGuGt
PdZCpIJ8cqerjH0zVVsiSl+OeMegLshkCjRfN8PgD+uHUFaWZBNwfP1hqeshZvDk
xqAzYmbiHZejy6PEmIr36ByBe9NiItuGJ0TFThcof9rdueQRal9fZO2O08ihTO3n
Cg4nxgVQh7LhOyxG/6Mt+iUxasDDUQlbxk2gFoO3EhiCl3NIxXt45OTEtlAXcxa1
54iLw8nRuGUfTjuyqf7vmzzluzFwxyp+60PI3wIDAQABAoIBAAEqU1UGR9Yhw/KF
9pwq6y9+dTPjOwFBNu2qLs9L7gsNDcAYWrku8YSjikwZnWyLQMHrsiT2clvBZK/e
OPTEonxMnO+rbq2KSA7XE2De52AMX663vq3LUW7n+VUvGPnlTmTk+SmYsByTh6Re
tv+8WQbZ1rohNxVIvO9vkcyaLHW0EkNDQVpIwzrO6IjM6vKycsNQ9dmLHY0/3T1Y
dvjgtuD/F9iuGayna8Sbv+Lt5bu7MR3xudMsTA1JSApiDb7GU9cmWu2ziVNg+FnT
ZK3wFyq0jiR1aJLshjEWufEF9S4f3LAq07dtZkLTRXpVgT8WI07IFKvHgsHjoqjY
KlJ5R2ECgYEA5QPJxnllBheYWNJU8vRsDMB1uZDUSdOHD24NBQh4zGSDW5fG82/c
aubKh8qaW48xSW2o++hJQeAXejnbHPIbGLwrOA+kKJXgFFJHrrzIeRF2/aUKpsFh
4YQABBK2cGK5x6AyG3p1hHmCNk/831dIrnd5U6DQYJ4LRRxI49ly+9ECgYEA3b6R
w4MDpUQQzU+dSggoyJ+/W0Nbb+8raoEjZ6AAqfo4JNQqSYnM2wY6vza6fVKaxNS8
GGoqe8kdfsF6ly8WF1afI8JMfJYtVLMfwsKGaaYmF9ZpmR8lRkQySxi7KQ0TcbdJ
wCiCR6OxIVJ50TE1P24blWwBxgL0mbpKjgLJla8CgYAKv7bEvgXj10+rO5QJIze/
EXl1EDsmi+sW6k9qIQ+qaD1SGzmXS3TI/7QZ04STL5FcpOz9hdWKZf40GmsSXLqw
2oQcyX8m+IHf8kyzAuFV7V/sX8a0NPdnIk7t4gL2G2wk1nwDlifV4+4cpnxz7yDW
L31eU3n0Tvawc7doGlivQQKBgQCjkYqGdONAiof2Wu8EiCZFb4lBMduGIx+cjavn
KaCzwc6eZB7ZZhvFyL+XAzDndwKRhPdG7zFtZDosoV3jnaknCA+V2iJ/mGvR2dvo
14M89YGN/eyhNddSEMYknRaaPnoEXRa692a6n6XulZ8kT68engMc4rIgNVfm+gM6
5BV9IwKBgQDGeMlFf7kwWxNzhcO6bCv/GNkFJLXqg9R7jAElBvaRVlzcS1eciNf3
5llPYju1YPJtOpQw73x0lNy9fA9opeB+QUV62owf7Bb2k8niK80rbqUfWBBgaHSP
QHovzlV6Wx5jkE+yU3rTXzLAmg2Jpcy4dkjEbB/JdbnRiNCjjX+hcw==
-----END RSA PRIVATE KEY-----
3. 生成根证书(用来对后续证书申请进行签名)
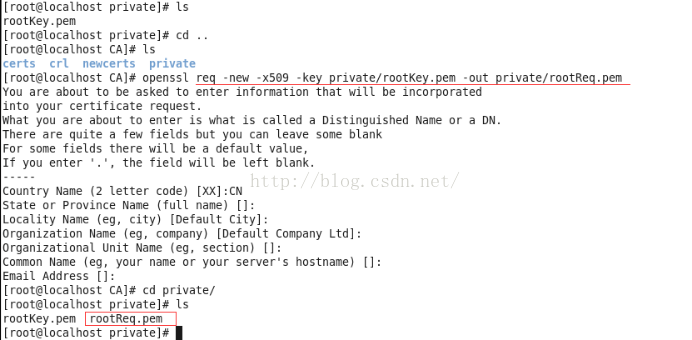
查看一下文件内容
[root@localhost private]# cat rootReq.pem
-----BEGIN CERTIFICATE-----
MIIDVzCCAj+gAwIBAgIJAMDqSttv4oGTMA0GCSqGSIb3DQEBBQUAMEIxCzAJBgNV
BAYTAkNOMRUwEwYDVQQHDAxEZWZhdWx0IENpdHkxHDAaBgNVBAoME0RlZmF1bHQg
Q29tcGFueSBMdGQwHhcNMTYwMTE4MTAzNzQxWhcNMTYwMjE3MTAzNzQxWjBCMQsw
CQYDVQQGEwJDTjEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZh
dWx0IENvbXBhbnkgTHRkMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
xl7AZiR6n1HW90vkKOmghhRpShiH+Cqtd8MkOa0b6h8er5zN0pAXqO6rUGYVYjIS
EZb7yIna5ecG0rlmZMxNwOWPJiV3q4a28CFkXpvCIRRvGuGtPdZCpIJ8cqerjH0z
VVsiSl+OeMegLshkCjRfN8PgD+uHUFaWZBNwfP1hqeshZvDkxqAzYmbiHZejy6PE
mIr36ByBe9NiItuGJ0TFThcof9rdueQRal9fZO2O08ihTO3nCg4nxgVQh7LhOyxG
/6Mt+iUxasDDUQlbxk2gFoO3EhiCl3NIxXt45OTEtlAXcxa154iLw8nRuGUfTjuy
qf7vmzzluzFwxyp+60PI3wIDAQABo1AwTjAdBgNVHQ4EFgQUfSkeLmCXyxLtPxD0
DdqQrDXj7zcwHwYDVR0jBBgwFoAUfSkeLmCXyxLtPxD0DdqQrDXj7zcwDAYDVR0T
BAUwAwEB/zANBgkqhkiG9w0BAQUFAAOCAQEAMsr3noTAgG1HxKan8VhIF63afMlF
f9xsUawY0mo3zXXFdQMTJ9Y/VkAwP8f2hXB+3qngfqXiNPY36ZtxudxeabXCMiCN
3wndIzDOrVHZMutwKpl9gpvOpBzKEcVHA5LezyzLLIc92cXbPzHMAapX7eZbTjlS
3h12E3HB0rZjoDbBrETdwz3FO/JpAXLHABlGMB595YJmhRmJeqSjU7Cyg5dTbryi
abBskrdqrpgJdRmow2Qdlvxt1nrpEkFPtu9Add5jhNCVozyHRzpM9RLETQRmD89+
0ru5l3GmfbYTl/jorpZ449hHriUjLZGobPfcYKLz++ZLTCHgxome0mk4VA==
-----END CERTIFICATE-----
生成个人证书
4. 为nginx生成密钥
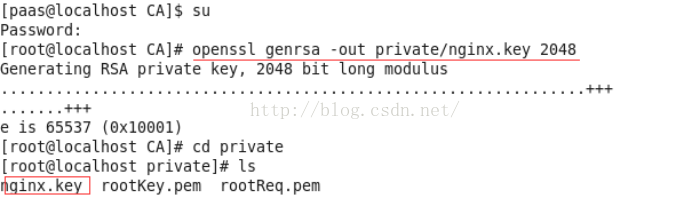
查看密钥内容
[root@localhost private]# cat nginx.key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwAPKfWtkZxRH77UMCjPiDpt/rrwDjWXVRR3YOLc/KF5zoZux
ZWw9Fm0xbHgfR6H956zVoPc8gwDUmy6e1NqOrPHb4baIbOpXuB2tZrEtIyf0EF1C
2rO8bGyoChy7rTbU2KcDFXfUA/jb1KzSn04KFPmsnarRGSDkcERir9E4geGZa+cM
ctrEXCi9MQw5XtUs7FpiqX2SDFtui62gaht6HvMwxyqm7sGNfL3WYPWMwFylsKNi
mitNlcAOGL/U7usH4PVRcukYH3DCgqd3TklwrdNtnbdhOqjdoBIvTY3IOxUP+9kb
ZufEcCXkBabHw+j04/TlI2S6INC4KFoOadPVqwIDAQABAoIBAHFMS1jB21ZvQxsP
yvDiOErCOg7SZY4zPiowN/sPNTcOtE/xXDUqLsli2LzWDC7qSLVA6DS4bX4nKUv/
sDyMUY9+jm2alNkfVW8QI9bqSGXsFzjorp/5Wf7oBichWSQVrHXB5jHuqK1HU/8j
kovpMk26HL5TolmfbOtJjqmLXDpV6nD+iKCMu7xLat5OBlX7NbkkJDqIeR0d+iRI
9bcvSa/rXlfVJCgqivsnkbq4iUQtdLPFzZQqxNMfDVSU3GPmOVpxOkas3e9EpS+u
4afil2M6XyDfIkN90TWT5OQ1RFESF95NhT6EqhOlVjP0MRgcTLXcH1hSLtV7Zfw7
9IIfacECgYEA9fXlDw/U66qR7VixElJLdnS23ZtTA1m2cWD+64rhg5kZKNy1cD2n
hW0UndxEPpyl2HjPg6xpp13kp95vJlaN4tA05rg3IRO/xtbIIM0InFQfMc+tHMzG
Kw8IzsukrzoDpkqk6orJxuaTtqp2jtMggPxYTl04ce+3X6YC6yi8MDsCgYEAx9o0
FIKlDvVpRWFtJEuC8u7k+9DYluVwp7nJ9HbBGa5R8i5AVQsC8jd/S9xDA55ksW6S
mcnVWB1gmzsbulWQElpB8P/J1Ug8MB0hA4y7G5+xiyHSladp8SF0LtDwwqLIFQt0
EJRyxuSTNf5YX4VGu5K1sp2KtCeoPOfaisrbiVECgYBNJoVkFRY3mfhOF8zrL08m
Z/PYTVlbqq9UnxU3MwgL7GD89UYgX+aFLrMR1T6+2QoYfcSxy8oUSppnoZkB0JKO
+7osSMpaIMS+DS8XQtkZmDV0vWzSpNTgOsYLf8s3f54XckCKpWAneLoKySuJH2aJ
rx3P7uO+sW+2m+88bjmhcwKBgEDquBARf9wkC1XmF7W6cYbH4smJRVF+peFVkCxA
huj4ntW0AGGfeg2DyW2y1nHOeZbI/AXIcex1XnQN9yvHr0zG1LSb4cvN8v8N9zNX
+081yE4RZn4GK3uQClVKuWn/xk5PshvQnJfOl6LqQ3qDqD41oZ+rXOq4FwXxqiN7
UWSBAoGBANCn50iL6zXbXYm7FCmdLpZW5iap2FaZjh/Y2OHnX9Vo7G8D71iSiUXL
mt4lRMNPiySNamNZIxJ4IYLhJz4AnBWdXj53eN2xPix6y/gUImJlrmQWEst0BXX5
05x8RTfo3jAG/8dIbs4X2JMqbbNKuMXWMFytXwT+AcaNB8wDLulH
-----END RSA PRIVATE KEY-----
5.为nginx生成证书申请
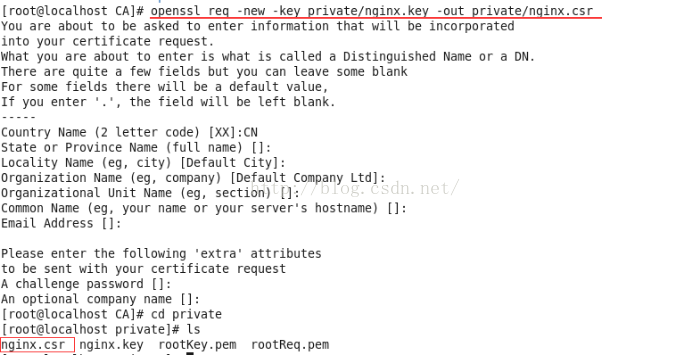
Note: 需要注意的是,Common Name一定要输nginx配置的域名,否则提示certificate has an invalid signature
查看证书申请内容
[root@localhost private]# cat nginx.csr
-----BEGIN CERTIFICATE REQUEST-----
MIIChzCCAW8CAQAwQjELMAkGA1UEBhMCQ04xFTATBgNVBAcMDERlZmF1bHQgQ2l0
eTEcMBoGA1UECgwTRGVmYXVsdCBDb21wYW55IEx0ZDCCASIwDQYJKoZIhvcNAQEB
BQADggEPADCCAQoCggEBAMADyn1rZGcUR++1DAoz4g6bf668A41l1UUd2Di3Pyhe
c6GbsWVsPRZtMWx4H0eh/ees1aD3PIMA1JsuntTajqzx2+G2iGzqV7gdrWaxLSMn
9BBdQtqzvGxsqAocu6021NinAxV31AP429Ss0p9OChT5rJ2q0Rkg5HBEYq/ROIHh
mWvnDHLaxFwovTEMOV7VLOxaYql9kgxbboutoGobeh7zMMcqpu7BjXy91mD1jMBc
pbCjYporTZXADhi/1O7rB+D1UXLpGB9wwoKnd05JcK3TbZ23YTqo3aASL02NyDsV
D/vZG2bnxHAl5AWmx8Po9OP05SNkuiDQuChaDmnT1asCAwEAAaAAMA0GCSqGSIb3
DQEBBQUAA4IBAQArQkrG8dkcnvj6EjK9WyUhisorHkcqqHv5S5P7uh9DxCgkOn1Z
0nBa0Nvsuz65PVLZdmrXPZCVbevZAO89dSFbMUnOIcUurVtlM5PAxdR0xNPa3k8d
WJu5gXA16JB9jzP+xmjvae4cA2eutoz4LH7tIoWnnLSmeZgWbJqw2yCNzj0ub2l8
9zGUXzn+71zk9y1pjRUDiqWzwno4fIwwVKotgqdhyublCodEdCYlnmFYIFxOJ6MB
36YG3KGG1QYaOO4R8F9DXEgX9azylk30kbbwjf+aU8Gz5Yfny2N9Y54P6Se9jniT
xfhLt4ZI/c20V/SG54T4FkgnWButVcUjS117
-----END CERTIFICATE REQUEST-----
6. 利用CA对证书申请进行签名
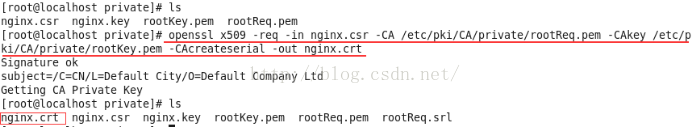
查看签名后的证书内容
[root@localhost private]# cat nginx.crt
-----BEGIN CERTIFICATE-----
MIIDADCCAegCCQDRRs1iBszBqDANBgkqhkiG9w0BAQUFADBCMQswCQYDVQQGEwJD
TjEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENvbXBh
bnkgTHRkMB4XDTE2MDExOTAyNTAyNloXDTE2MDIxODAyNTAyNlowQjELMAkGA1UE
BhMCQ04xFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UECgwTRGVmYXVsdCBD
b21wYW55IEx0ZDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMADyn1r
ZGcUR++1DAoz4g6bf668A41l1UUd2Di3Pyhec6GbsWVsPRZtMWx4H0eh/ees1aD3
PIMA1JsuntTajqzx2+G2iGzqV7gdrWaxLSMn9BBdQtqzvGxsqAocu6021NinAxV3
1AP429Ss0p9OChT5rJ2q0Rkg5HBEYq/ROIHhmWvnDHLaxFwovTEMOV7VLOxaYql9
kgxbboutoGobeh7zMMcqpu7BjXy91mD1jMBcpbCjYporTZXADhi/1O7rB+D1UXLp
GB9wwoKnd05JcK3TbZ23YTqo3aASL02NyDsVD/vZG2bnxHAl5AWmx8Po9OP05SNk
uiDQuChaDmnT1asCAwEAATANBgkqhkiG9w0BAQUFAAOCAQEAZbHdnO27DIaAWpuJ
b2bQeMSPW/CBeRf3b9JUz3Rq2loEse8ENSfxAwMGlJ1PGv7IucEZNnOxoMcsjuhN
4IoE1YkSEEC1J4dKxOwuiYqoQi93skKSGGHQWKTqjqUa2cELtK6iIoIHxPbwbQ6G
e/KJsDYN5FukkA73402QkfbmBR8sOMCxNWgWiscmrXP5/gj7R86ef5d0VvNxlim8
dFnPqpXlpsPhmd7kgY7tJIG4BYOaNzgVHvQeDlAlBDqRaPf5dxPw85NFE4E2gIDC
YhiYsrRhaguat0AWtB0N/LTqHKgQkjbm7fo9ttPH2p1BOUXiWxzvEOQRCKSizEYG
b7T8JA==
-----END CERTIFICATE-----
配置Nginx SSL
7.将SSL证书拷贝到Nginx某个配置目录,并配置nginx
演示中将nginx.crt和nginx.key拷贝到/home/paas/nginx/config目录下

配置nginx.conf
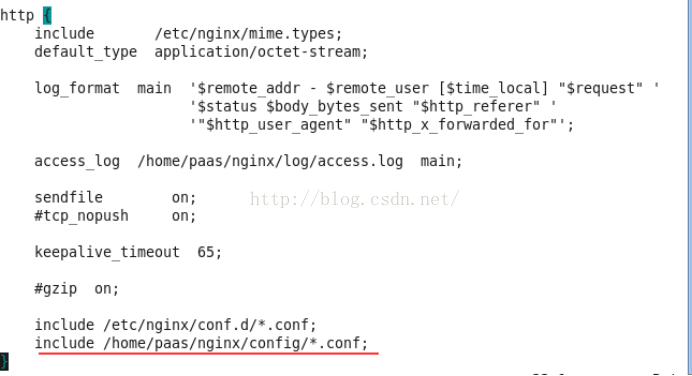
配置nginx的ssl参数(本例中是在/home/paas/nginx/config/exampleSSL.conf)
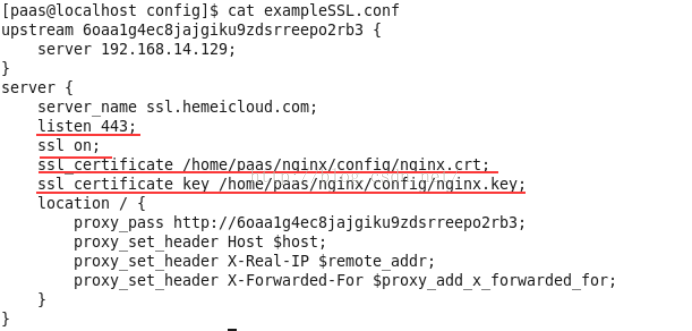
重启nginx,在CentOS中打开浏览器,访问https://www.gworg.com ,就能看到熟悉的nginx welcome页面了。
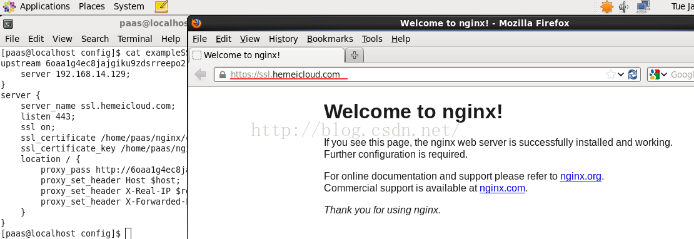
8. 配置在windows中访问
a) 修改hosts文件,将<CentOS IP>和ssl.hemeicloud.com加入
b) 将443端口加入防火墙过滤器中
/sbin/iptables -I INPUT -p tcp --dport 443 -j ACCEPT 加tcp 80端口加入防火墙中,允许外部访问tcp 80端口
/etc/init.d/iptables save 保存防火墙设置
/etc/init.d/iptables restart 重启防火墙
在chrome浏览器,提示不是私密连接


