Centos6.3下Apache配置https证书访问
这里简单演示一下Apache下基于加密的认证访问—-https加密方式访问。
1.DNS解析这里不再赘述了哈,相见本次演示的dns解析情况:
[root@localhost html]# nslookup www.abc.comServer: 192.168.2.115Address: 192.168.2.115#53Name: www.abc.comAddress: 192.168.2.115
2.安装Apache SSL支持模块:# yum install -y mod_ssl (默认yum安装httpd是没有安装该模块的,安装后自动生产/etc/httpd/conf.d/ssl.conf文件)并生成证书。
[root@localhost certs]# pwd/etc/pki/tls/certs[root@localhost certs]# lsca-bundle.crt index.html localhost.crt Makefileca-bundle.trust.crt localhost1.crt make-dummy-cert[root@localhost certs]# openssl req -utf8 -new -key ../private/localhost.key -x509 -days 3650 -out abc_com.crtYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter ‘.’, the field will be left blank.—–Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:510510Locality Name (eg, city) [Default City]:GZOrganization Name (eg, company) [Default Company Ltd]:ABC.COMOrganizational Unit Name (eg, section) []:Mr.ZhangCommon Name (eg, your name or your server’s hostname) []:www.abc.comEmail Address []:root@abc.com[root@localhost certs]#
3.配置Apache,基本配置这里不多说了,下面是配置www.abc.com站点http访问的情况。
[root@localhost html]# tail -n 8 /etc/httpd/conf/httpd.confNameVirtualhost 192.168.2.115:80<VirtualHost www.abc.com:80>ServerAdmin webmaster@dummy-host.example.comDocumentRoot /var/www/htmlServerName www.abc.comErrorLog logs/dummy-host.example.com-error_logCustomLog logs/dummy-host.example.com-access_log common</VirtualHost>[root@localhost html]# tail /var/www/html/index.htmlwww.abc.com[root@localhost html]#
4.配置Apache支持https访问www.abc.com站点,编辑 vim /etc/httpd/conf.d/ssl.conf 文件,制定www.abc.com站点https访问时的相关信息。添加下面配置。
<VirtualHost www.abc.com:443>DocumentRoot “/var/www/html/www.kuteatest.net” #//为了显示效果,这里的站点目录不一样,一般情况一个域名应该指向同一目录的。ServerName www.abc.com:443ErrorLog logs/ssl_error_logTransferLog logs/ssl_access_logLogLevel warnSSLEngine onSSLProtocol all -SSLv2SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOWSSLCertificateFile /etc/pki/tls/certs/abc_com.crtSSLCertificateKeyFile /etc/pki/tls/private/localhost.key<Files ~ “\.(cgi|shtml|phtml|php3?)$”>SSLOptions +StdEnvVars</Files><Directory “/var/www/cgi-bin”>SSLOptions +StdEnvVars</Directory>SetEnvIf User-Agent “.*MSIE.*” \nokeepalive ssl-unclean-shutdown \downgrade-1.0 force-response-1.0CustomLog logs/ssl_request_log \“%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \”%r\” %b”</VirtualHost>
4.重启Apache服务,测试访问。
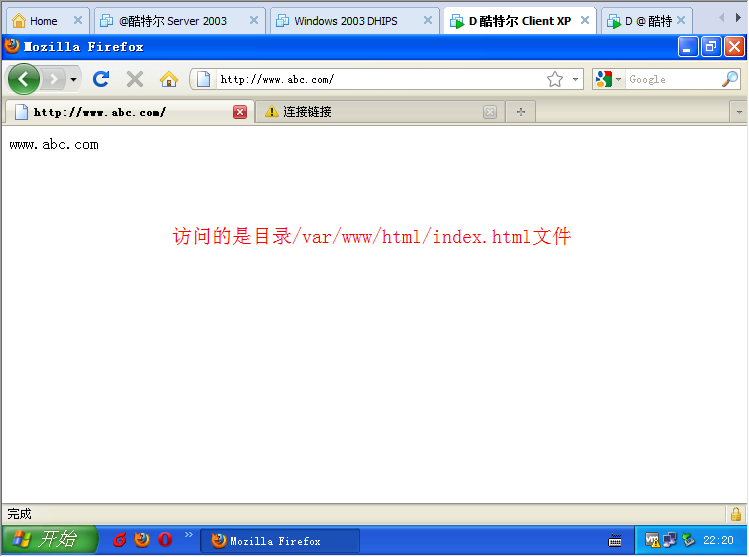
测试http访问的结果
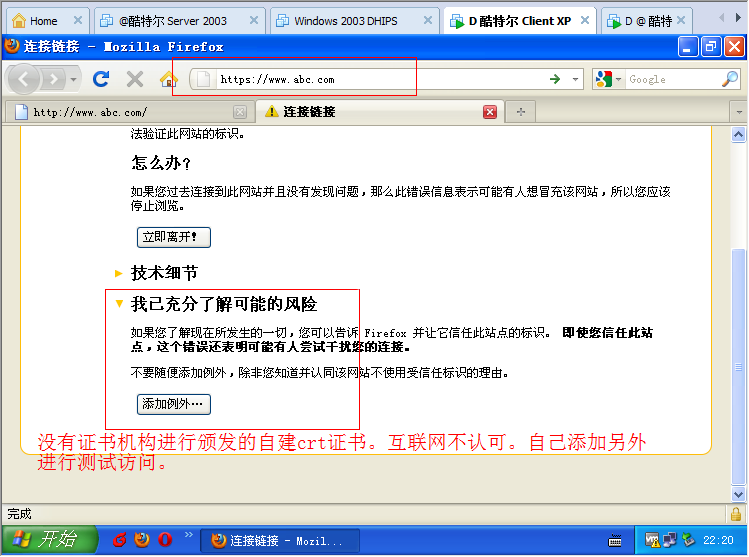
测试https访问的结果
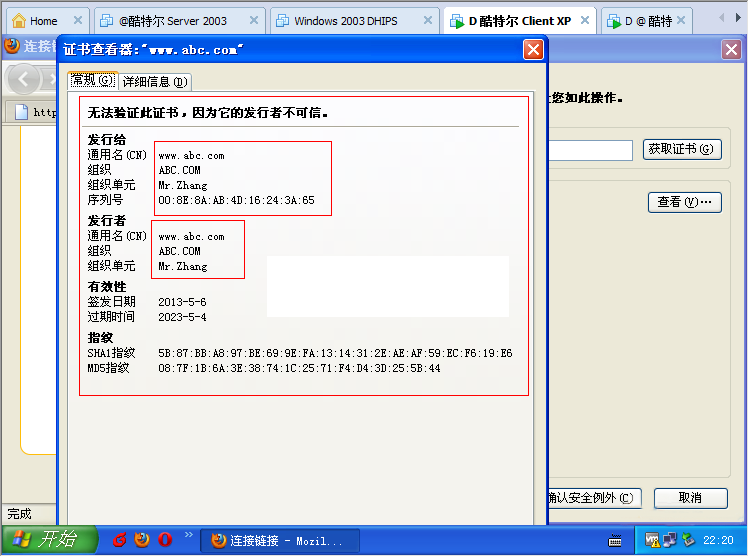
查看证书信息和自建crt信息一致
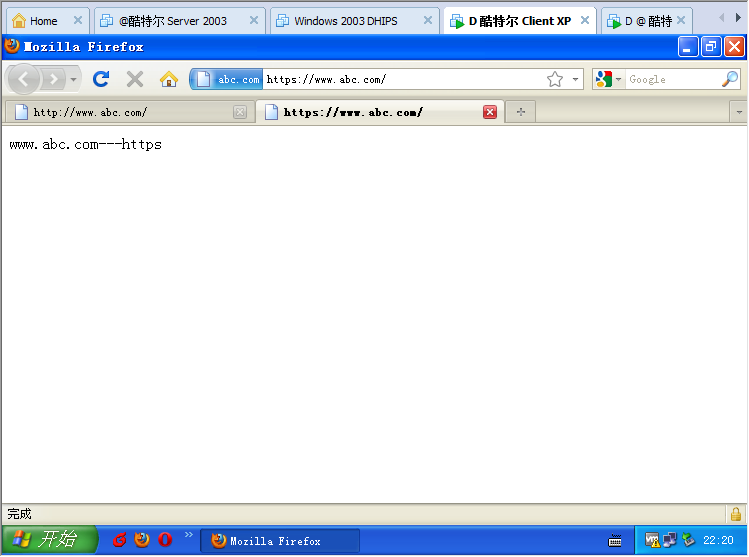
https访问的最终结果


